Background:
The first step when helping a customer set-up AWS credentials is to ask their IT department if they have:- Keys for a user with TranslateFullAccess and AmazonS3FullAccess policies
- An S3 bucket that user has access to
Access:
Configuring the AWS Configuration in AI Hub, will enable the customer to access all available services via the AWS Bedrock ecosystem, including:- Amazon Titan Express
- AI21 Labs
- Anthropic Claude Models via Bedrock (Sonnet 4.5, Haiku 4.5, Opus 4.1, and Opus 4.5) for LILT Create
- Amazon Textract
- Amazon Transcribe
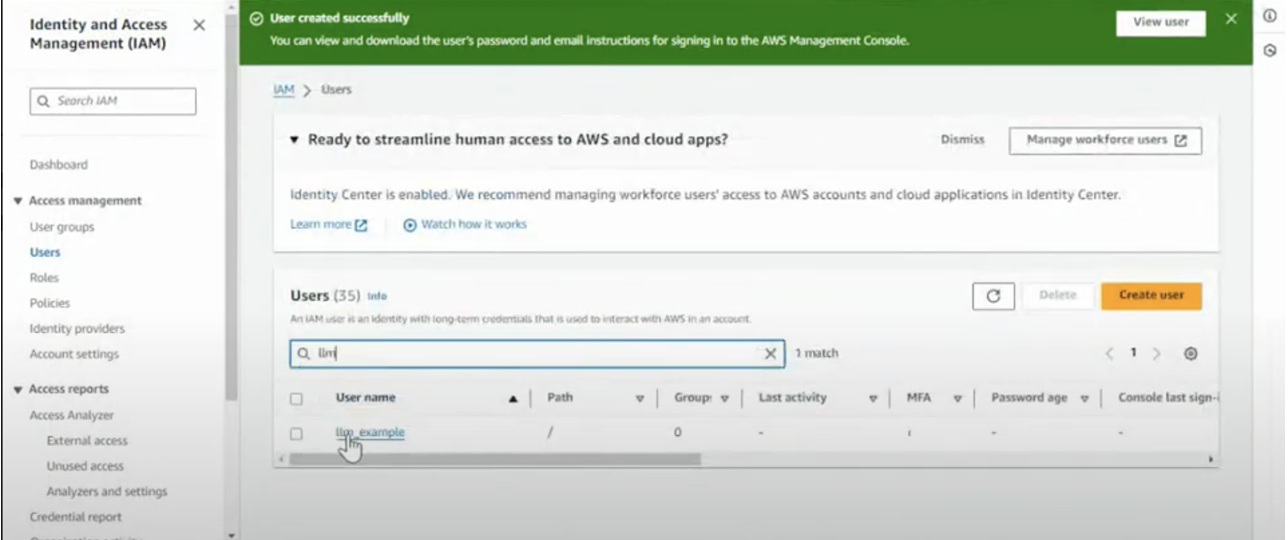
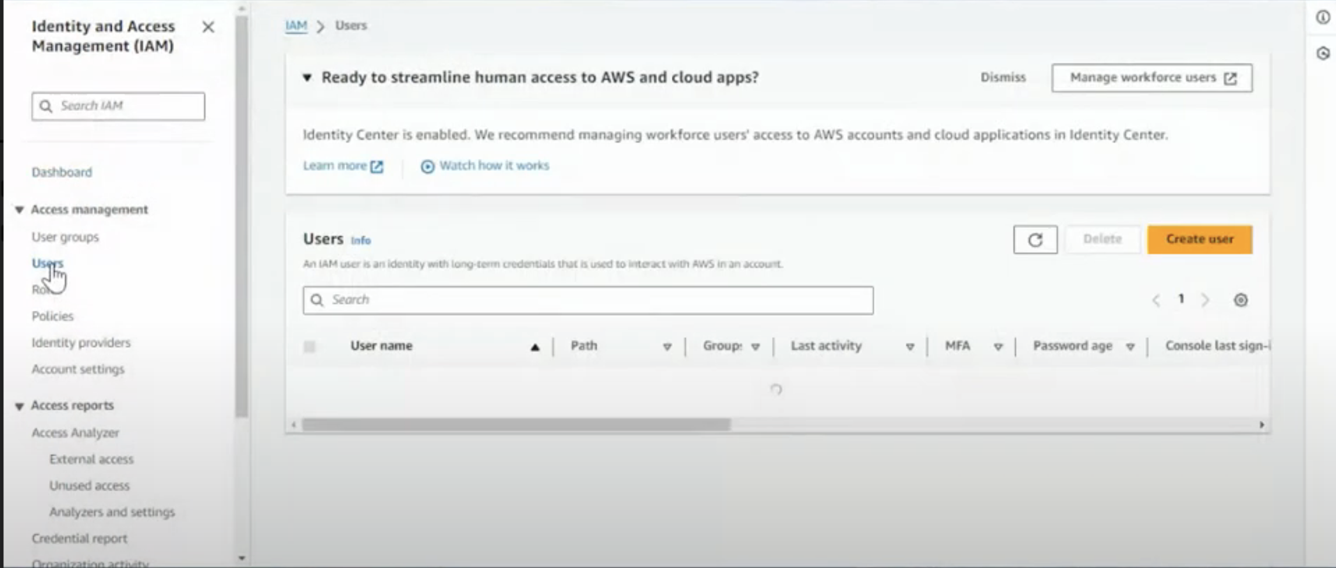
Create a new user
- Search for IAM and select IAM.
- Select Users, “Create User”
-
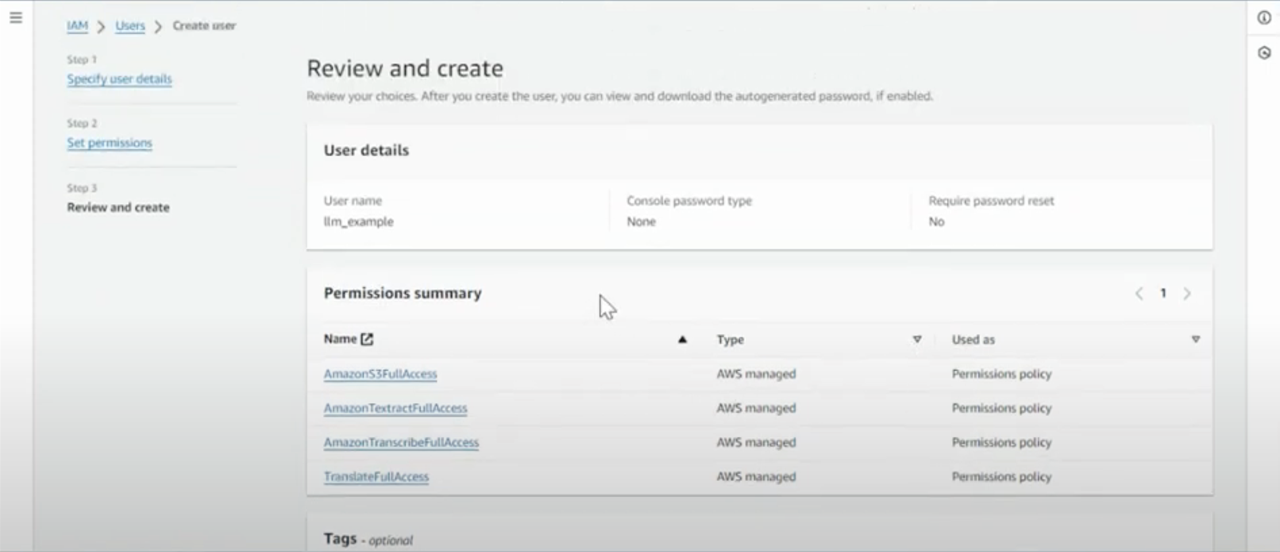
- You do not need to select “Provide user access to the AWS Management Console”
- Attach policies directly
- TranslateFullAccess
- AmazonS3FullAccess
- AmazonTextractFullAccess (OCR Only)
- AmazonTranscribeFullAccess (ASR only)
-
- Now click Create User
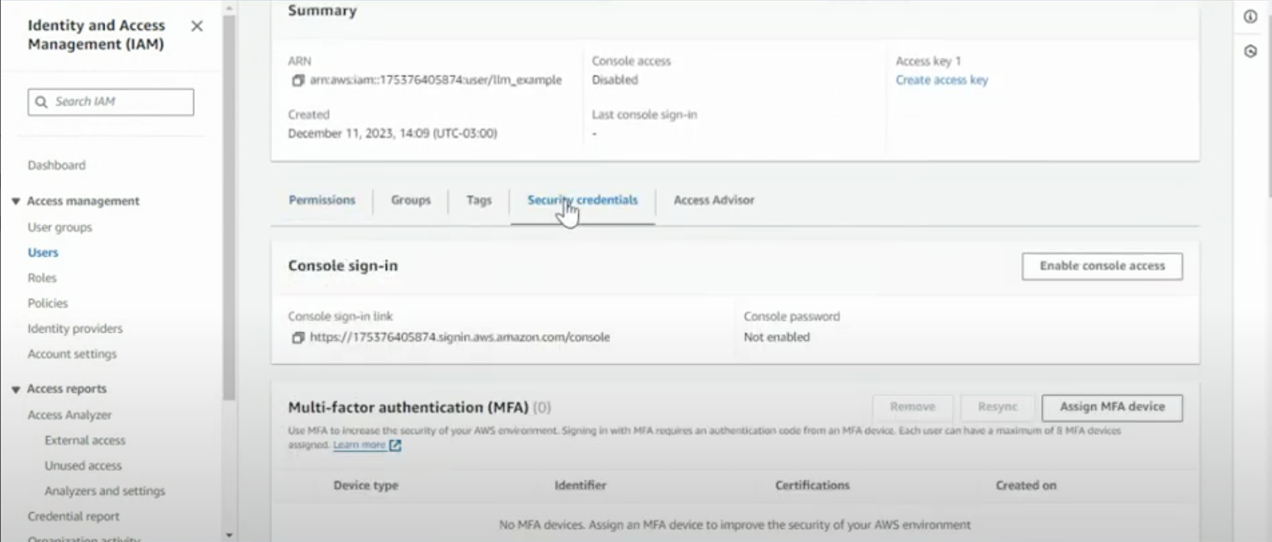
- Search for the user created in the previous step and select
-
- Click Security credentials
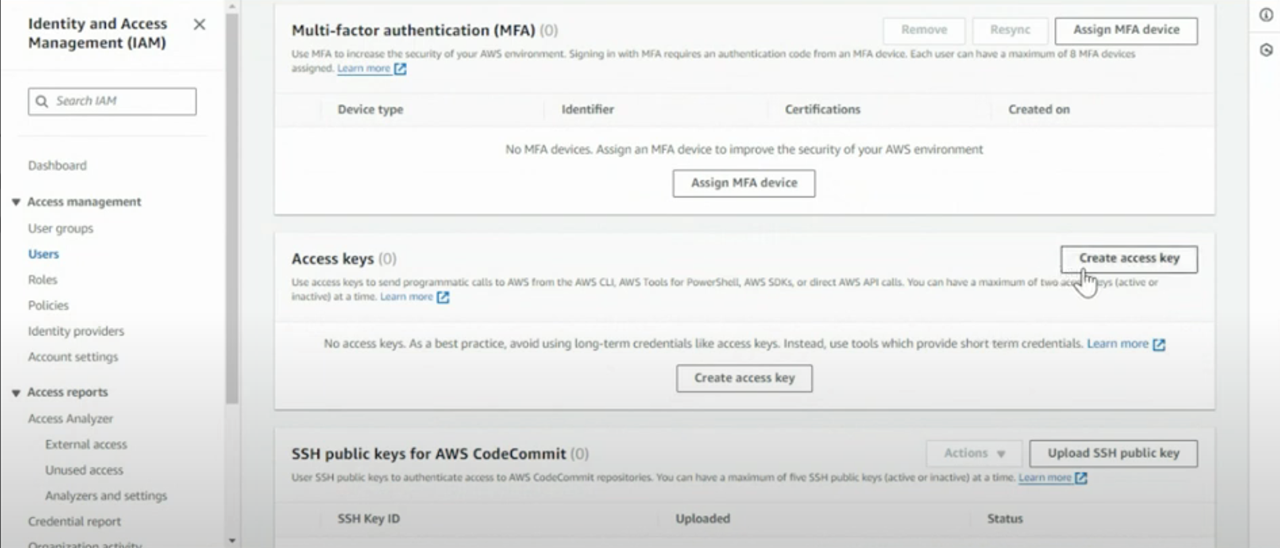
-
- Click “Create access key”
-
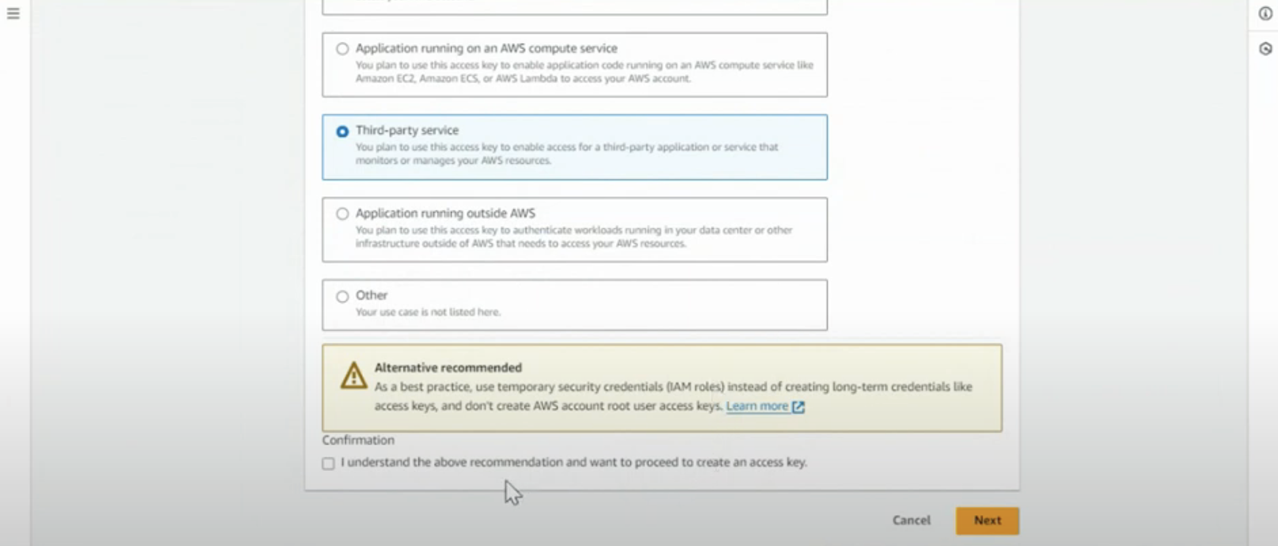
- Select Third-party service, select Next
-
- Name the key
- Download .csv file this is your “AWS Access Key ID” and “AWS secret access key”. You will not be able to recreate the .csv
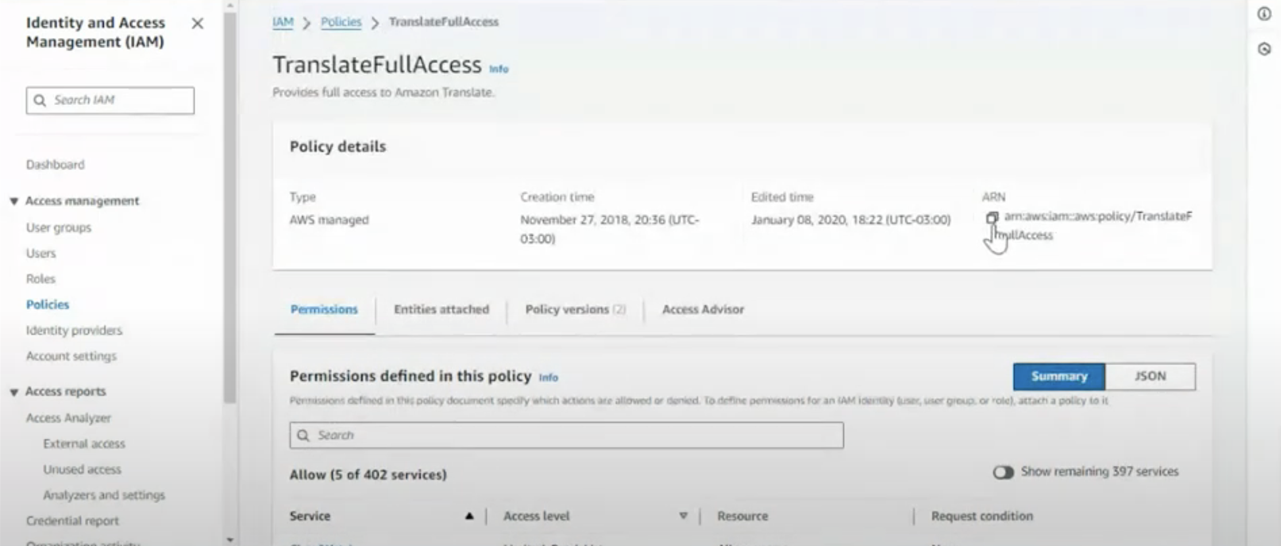
Create AWS data access ARN
- Search for the user you created in “Create user” steps
- Click into the user
- Scroll down to Permissions policies
- Select “TranslateFullAccess”
- The ARN will be on the top right
Create S3 Bucket
- Type in S3 in bar
- Click S3
- Create Bucket
-
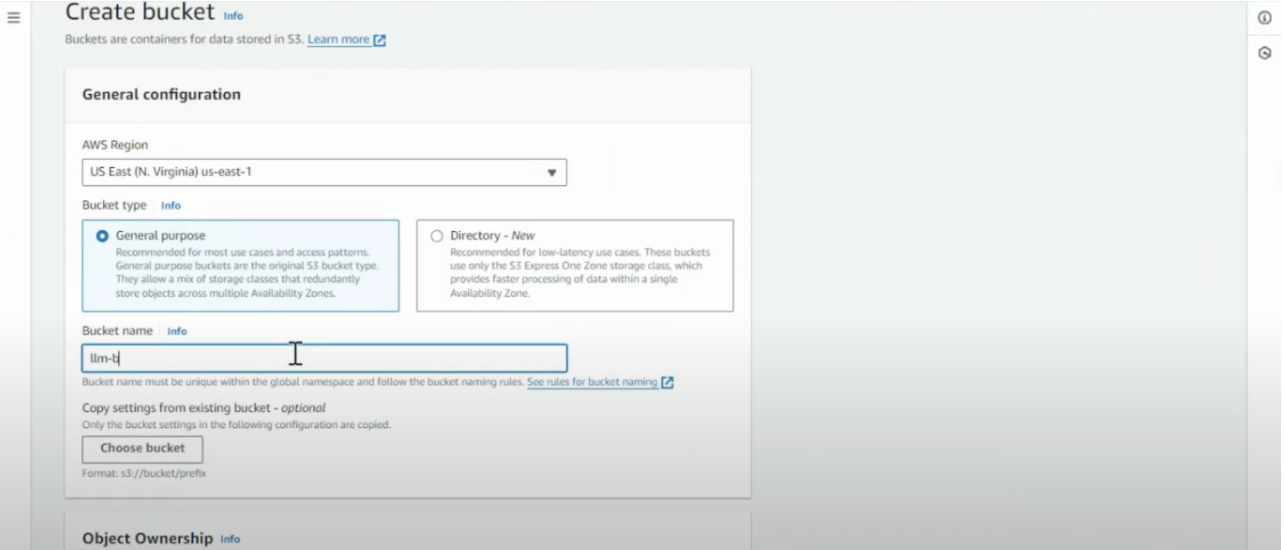
- Choose an AWS region
- We reccommend US-EAST-1
- Select a General purpose
- Name the bucket
-
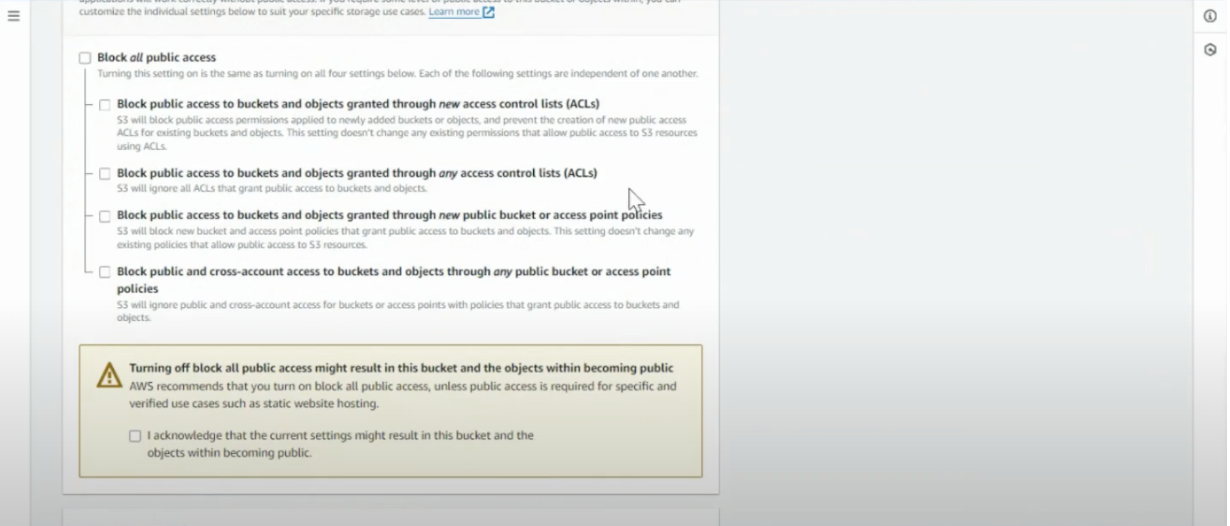
- Unselect “block public access”
-
- Disable Bucket versioning
-
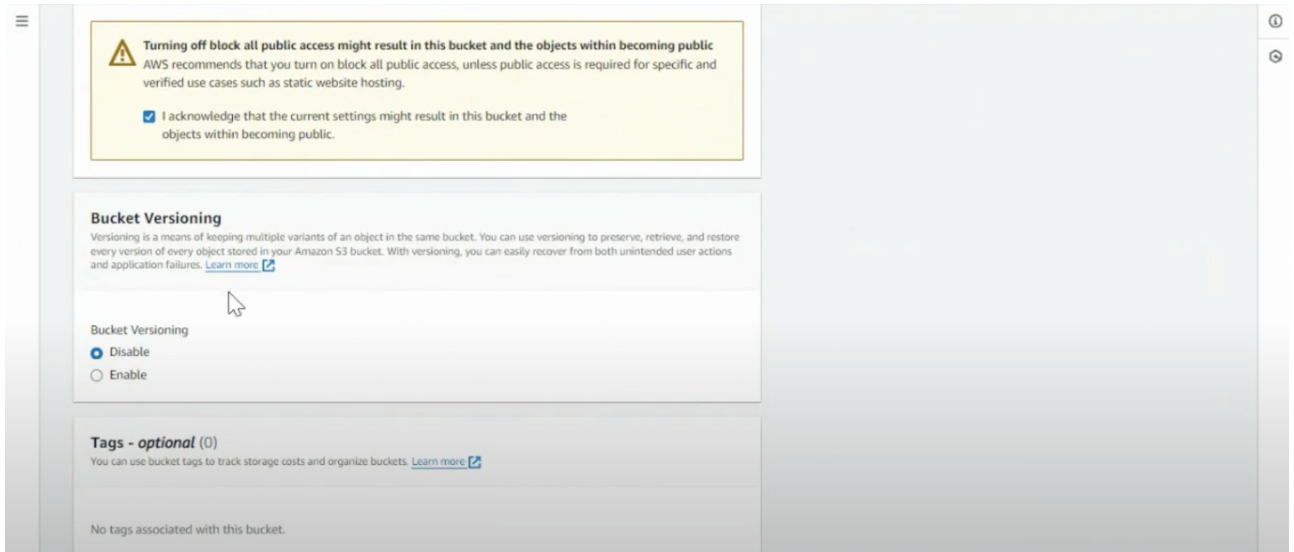
- (Optional) we recommend that you add a LILT tag, so that you can track your usage
-
- Click create the bucket
-
-
- Enter this bucket name into LILT’s Amazon credentials, and select the region the Bucket is assigned